Ensuring Platform Integrity and Data Protection
At Culturefy, protecting your data is foundational to everything we do. We have engineered a security framework that ensures platform integrity, protects sensitive information, and strengthens trust across all interactions.
Ensuring Platform Integrity and Data Protection
At Culturefy, protecting your data is foundational to everything we do. We have engineered a security framework that ensures platform integrity, protects sensitive information, and strengthens trust across all interactions.
Ensuring Platform Integrity and Data Protection
At Culturefy, protecting your data is foundational to everything we do. We have engineered a security framework that ensures platform integrity, protects sensitive information, and strengthens trust across all interactions.
Ensuring Platform Integrity and Data Protection
At Culturefy, protecting your data is foundational to everything we do. We have engineered a security framework that ensures platform integrity, protects sensitive information, and strengthens trust across all interactions.

Enterprise-Grade Security and Compliance
Engineered on Proven SOC 2 and GDPR-Compliance Standards with Microsoft Azure at it's Core
Role-Based Access Control (RBAC) for secure user authentication
Prevention of unauthorized data exposure through AI model interactions
Safeguarding sensitive company data across public LLMs
Role-Based Access Control (RBAC) for secure user authentication
Prevention of unauthorized data exposure through AI model interactions
Safeguarding sensitive company data across public LLMs
Automated redaction of Personally Identifiable Information (PII)
Enforcement of encryption standards for data in transit
A multi-tenancy security framework to protect tenant data integrity
Automated redaction of Personally Identifiable Information (PII)
Enforcement of encryption standards for data in transit
A multi-tenancy security framework to protect tenant data integrity
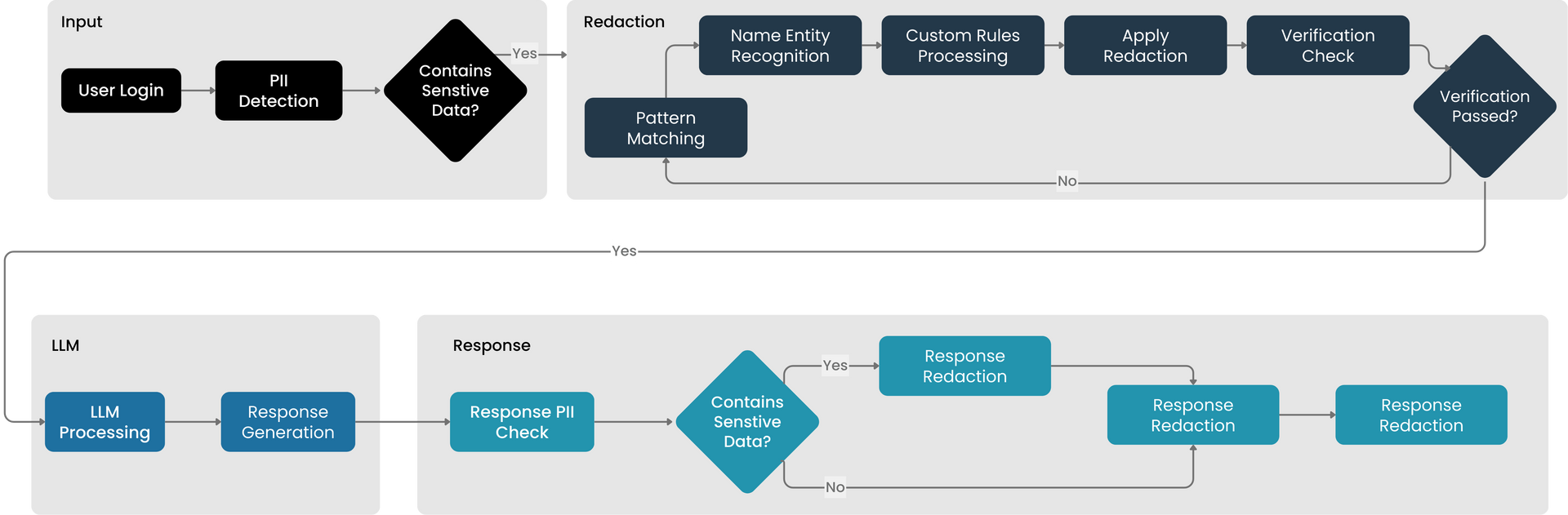
Role-Based Access Control Framework
We enforce strict enterprise-level security and data governance using RBAC:
- All user activities are logged and audited
- Access permissions are enforced dynamically
- Unauthorized attempts are denied at the interaction layer.
Role-Based Access Control Framework
We enforce strict enterprise-level security and data governance using RBAC:
- All user activities are logged and audited
- Access permissions are enforced dynamically
- Unauthorized attempts are denied at the interaction layer.

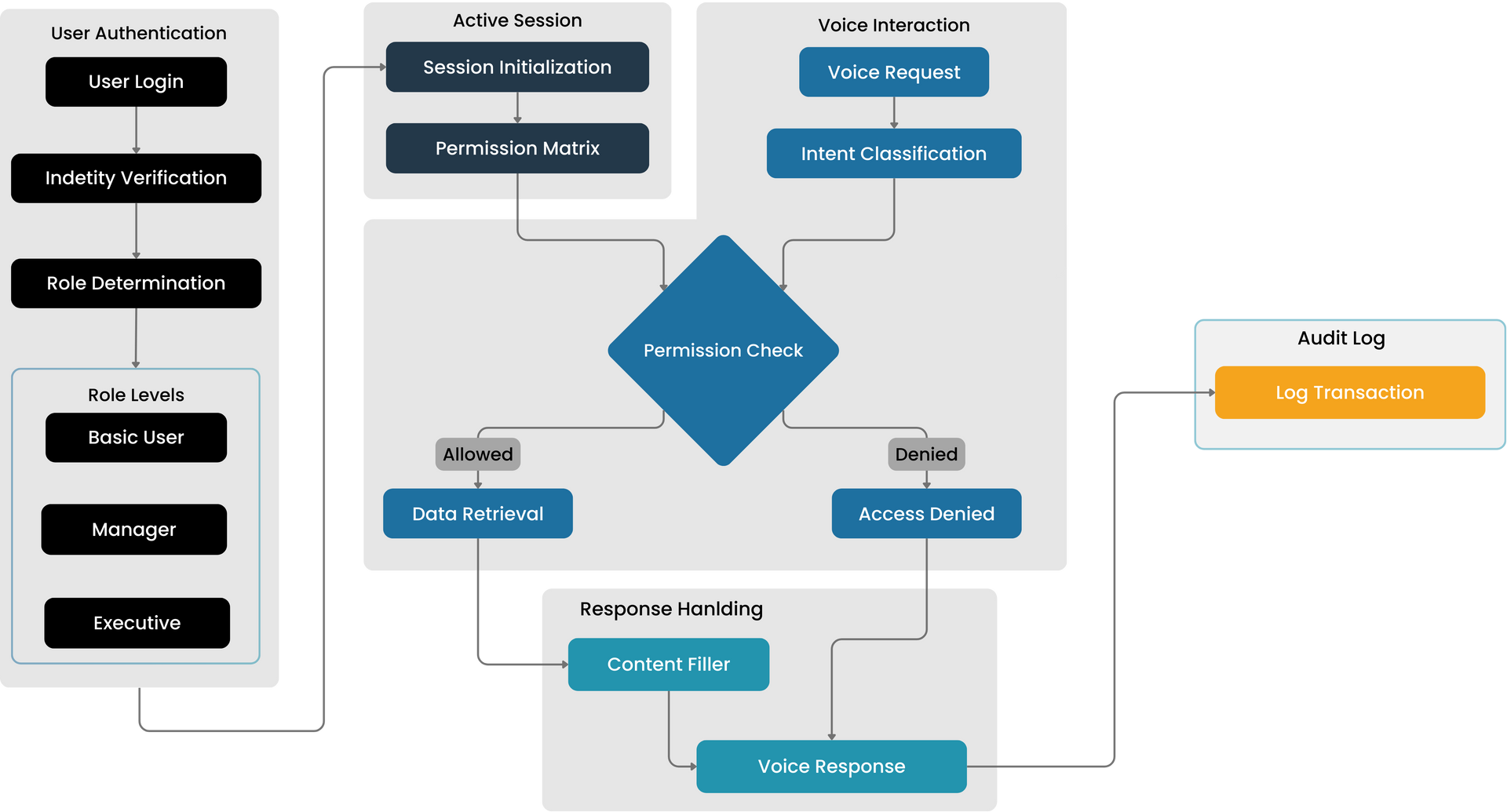
Comprehensive Security Overview
Our security architecture is built around a permission matrix and session management system that includes:
- Identity verification and role determination
- Role-based access permissions for Basic Users, Managers, Executives, and Content Fillers
- Active session monitoring, voice interaction auditing, and secure response handling
- Real-time permission checks and access control.

Comprehensive Security Overview
Our security architecture is built around a permission matrix and session management system that includes:
- Identity verification and role determination
- Role-based access permissions for Basic Users, Managers, Executives, and Content Fillers
- Active session monitoring, voice interaction auditing, and secure response handling
- Real-time permission checks and access control.
Data Encryption at Rest
Culturefy ensures that all data is protected throughout its lifecycle with:
- AES-256 encryption at rest
- Customer-controlled key management, providing enterprises full control over encryption keys.
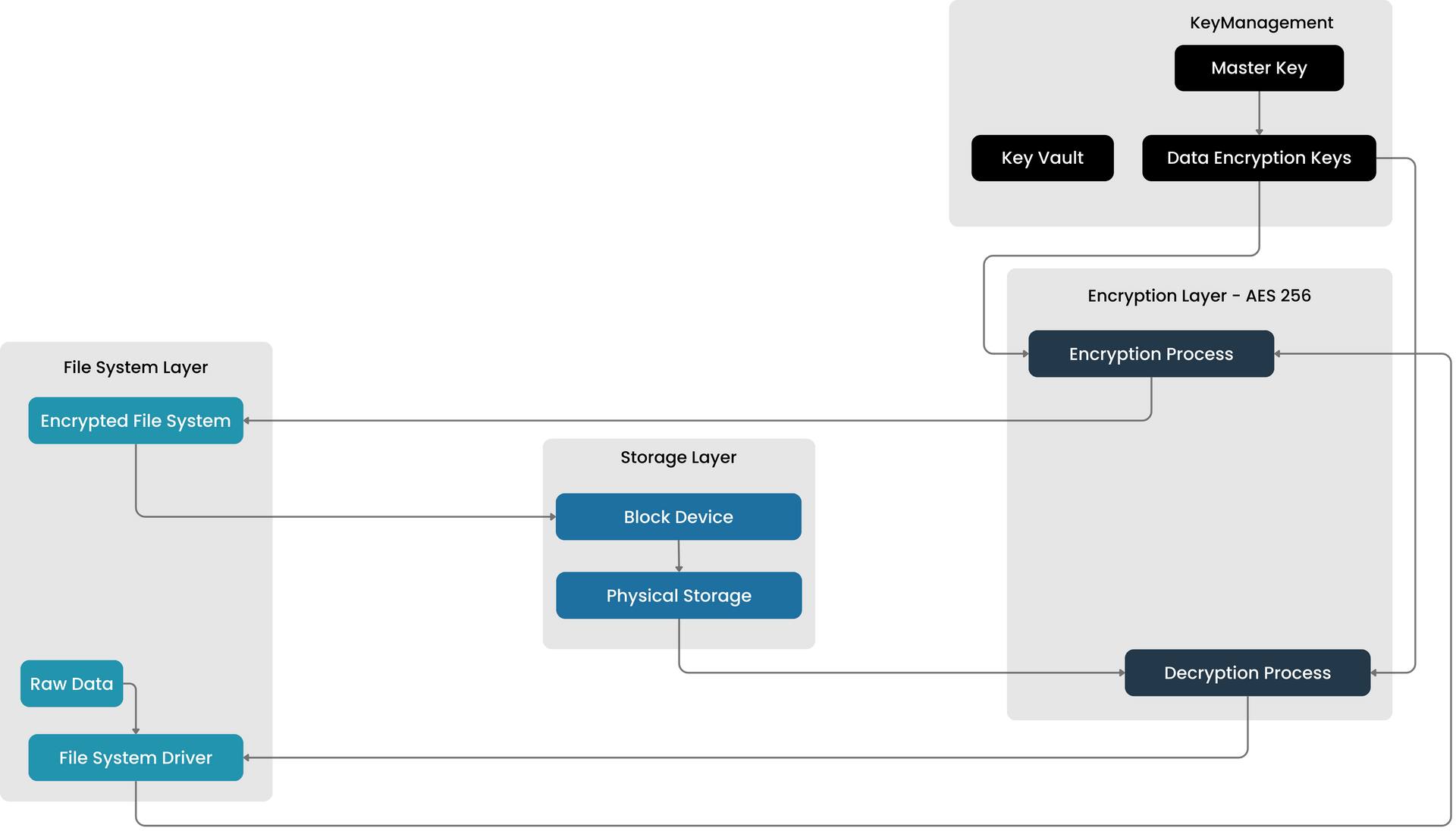
Data Encryption at Rest
Culturefy ensures that all data is protected throughout its lifecycle with:
- AES-256 encryption at rest
- Customer-controlled key management, providing enterprises full control over encryption keys.

Certificate Pinning for Data Transfers
We collaborate with tenants to implement certificate pinning, further securing data transfers by:
- Validating server certificates against pinned values
- Establishing encrypted channels
- Reducing risks associated with certificate-based vulnerabilities.

Certificate Pinning for Data Transfers
We collaborate with tenants to implement certificate pinning, further securing data transfers by:
- Validating server certificates against pinned values
- Establishing encrypted channels
- Reducing risks associated with certificate-based vulnerabilities.
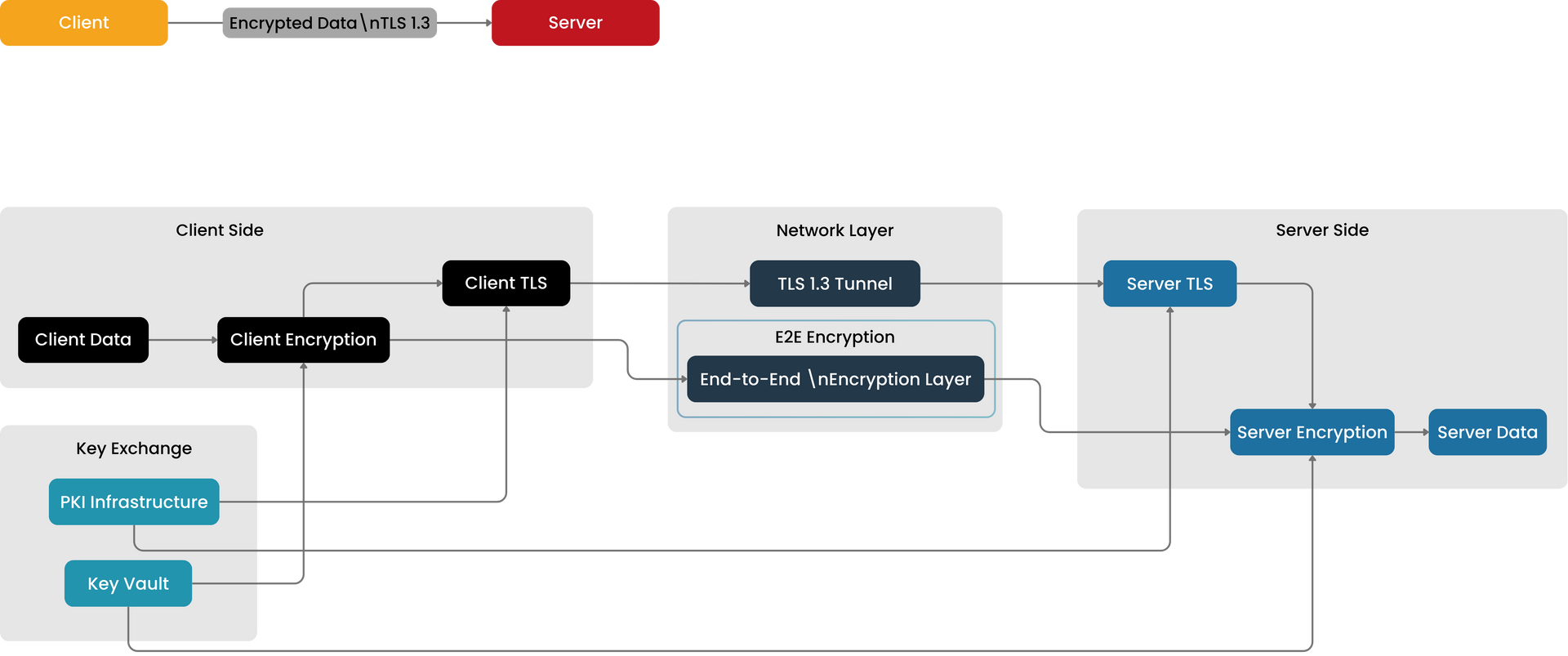
Data Encryption in Transit
To maintain confidentiality and security during data transfers, we use:
- TLS 1.3 encryption protocols for data in transit
- End-to-end encryption to protect sensitive information
- Tenant-controlled key management for additional control and compliance.
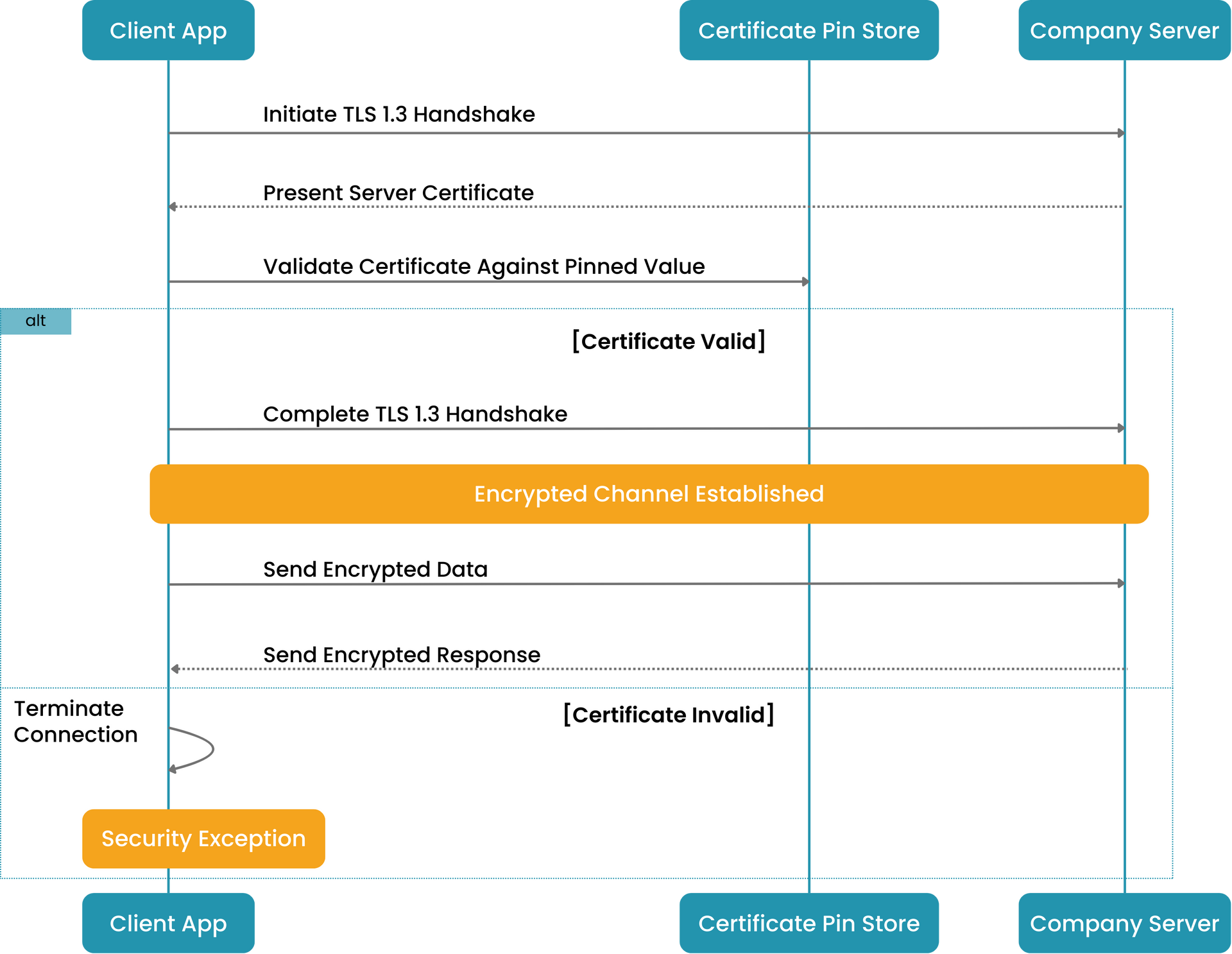
Data Encryption in Transit
To maintain confidentiality and security during data transfers, we use:
- TLS 1.3 encryption protocols for data in transit
- End-to-end encryption to protect sensitive information
- Tenant-controlled key management for additional control and compliance.

Protecting Tenant Data Integrity
We ensure complete tenant data segregation and integrity through:
- Dedicated resources for each tenant
- Isolated databases
- Segregated application and infrastructure layers This architecture prevents unauthorized access and guarantees sensitive information protection.
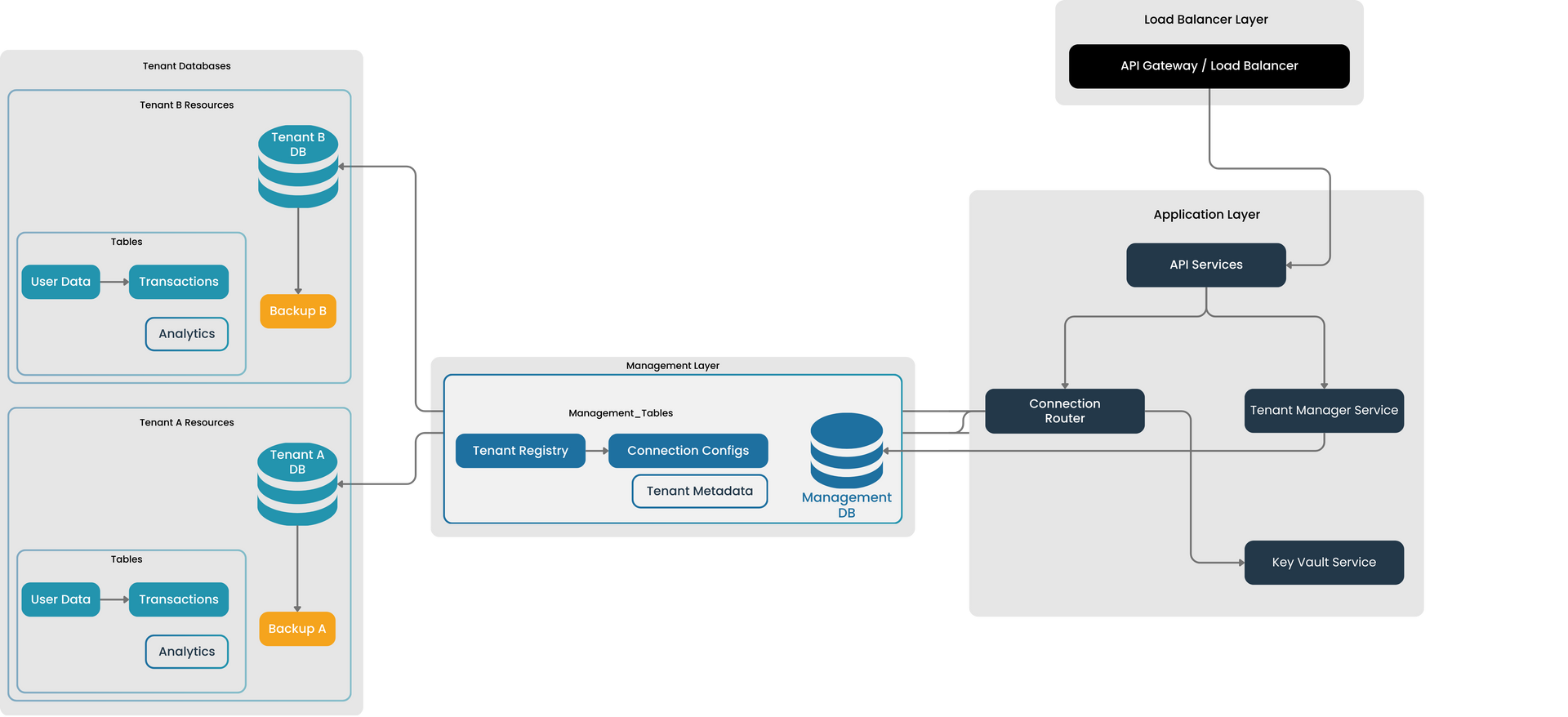

Protecting Tenant Data Integrity
We ensure complete tenant data segregation and integrity through:
- Dedicated resources for each tenant
- Isolated databases
- Segregated application and infrastructure layers This architecture prevents unauthorized access and guarantees sensitive information protection.
Built on a Secure and Compliant Foundation
Our platform infrastructure is fully aligned with:
- SOC 2 Type II compliance standards
- GDPR regulatory requirements We partner with Microsoft Azure and industry-leading services to maintain the highest levels of security and operational trust.

Built on a Secure and Compliant Foundation
Our platform infrastructure is fully aligned with:
- SOC 2 Type II compliance standards
- GDPR regulatory requirements We partner with Microsoft Azure and industry-leading services to maintain the highest levels of security and operational trust.


